Security¶
Standard measures¶
To prevent unauthorized access to the SCWS, a number of security measures built in the operating system and the standard browsers are taken advantage of.
Network restriction¶
First, the SCWS is listening only to the 127.0.0.1 interface (localhost). This prevents any connection from the network. Only local processes can therefore contact the service.
Cross-origin restriction¶
In addition, the Cross-Origin Resource Sharing (CORS) mechanism, implemented by all browsers, prevents pages served by unauthorized servers to access the service. The value of the Access-Control-Allow-Origin HTTP header returned by the service is determined by the Web Application Certificate, and page originating from a different server will be denied access.
Proprietary authentication scheme¶
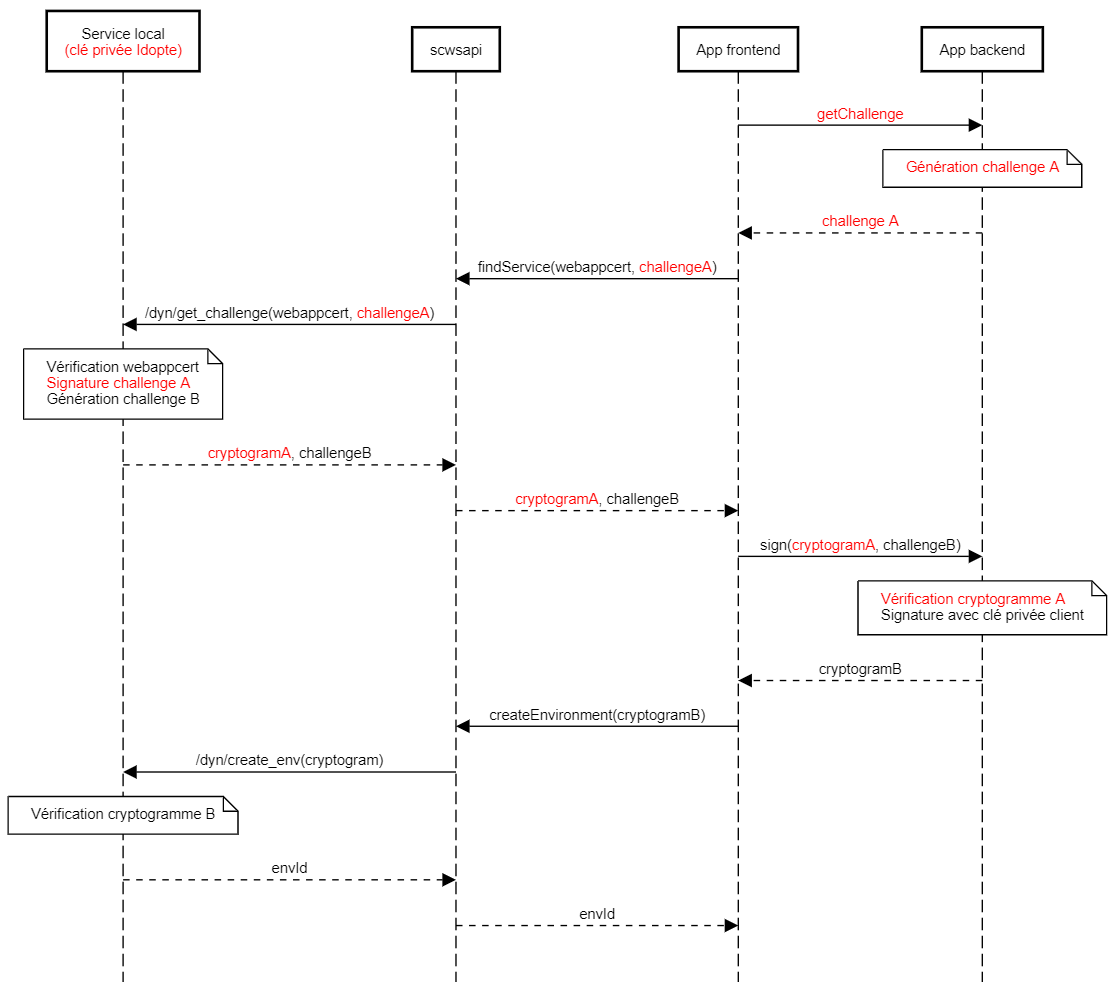
In addition to the measures described above, a proprietary scheme, using public key cryptography and challenge-response, has been defined to ensure that only authorized web applications can use the service, and also for web applications to authenticate the service.
When the web application initially contacts the SCWS (through a SCWS.findService() call), it must provide a static Web Application Certificate, generated by Idopte for each web application, and a random challenge. The Web Application Certificate, given as a string, certifies the server URL and is used in combination with the CORS mechanism to ensure the web application is legitimate.
The challenge, given as a hexadecimal string, will be signed by local service using the Idopte private key. As a result to this call, the web application will receive the corresponding cryptogram, which can be verified with the right Idopte public key, to authenticate the local service the web application is communicating with.
The public key to use for cryptogram verification can be found in the IdoptePublicKeys file provided by Idopte. The web application should parse this file, and use the keyID returned by the SCWS.findService() call to retrieve the appropriate public key in the file.
This file contains a list of public keys, given as PEM data. When a key is revoked, its data contained between -----BEGIN PUBLIC KEY----- and -----END PUBLIC KEY----- is replaced by !REVOKED!. Parsing examples of this file are given in Environment setup chapter. Note that this file may evolve in the future.
Moreover, the web application is also given a challenge as a result of the SCWS.findService() method call. This challenge must be signed on the application server side, and the signature must be sent back to the client side and transmitted to the SCWS (through a SCWS.createEnvironment() call). This will then grant access to all subsequent calls to API functions.
Note that, for this scheme to make sense, the server must be able to identify that the challenge signature or verification request comes from a genuine client. This is the responsiblity of the web application developer to guarantee this (for example using cookies, or the session mechanisms provided by the server-side framework).
See the Environment setup chapter for more information.